Right on man I get that and of course Russia hacks USA all day every day. Ill give you one sample to read through if you wanna take the time.
A Russian IP was used , which is literally my point of anyone that "hacks" won't use their own geo IP.
https://www.wordfence.com/blog/2016/12/russia-malware-ip-hack/
https://nypost.com/2017/08/15/new-report-claims-dnc-hack-was-an-inside-job-not-russia/
The United States government earlier this year
officially accused Russia of interfering with the US elections. Earlier this year on October 7th, the Department of Homeland Security and the Office of the Director of National Intelligence
released a joint statement that began:
“
The U.S. Intelligence Community (USIC) is confident that the Russian Government directed the recent compromises of e-mails from US persons and institutions, including from US political organizations. The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts.”
Yesterday the
Obama administration announced that they would expel 35 Russian diplomats and close two Russian facilities in the United States, among other measures, as punishment for interfering with the US 2016 election.
In addition, yesterday the Department of Homeland Security (DHS) and the Office of the Director of National Intelligence (DNI)
released a Joint Analysis Report, or JAR, compiled by the DHS and FBI, which they say attributes the election security compromises to Russian intelligence operatives that they have codenamed ‘
GRIZZLY STEPPE‘.
The report that DHS and DNI released includes in its first paragraph: “
This document provides technical details regarding the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints associated with the U.S. election, as well as a range of U.S. Government, political, and private sector entities. The report contains specific indicators of compromise, including IP addresses and a PHP malware sample.”
At Wordfence our focus is WordPress security. Our security analysts spend a lot of time analyzing PHP malware, because WordPress is powered by PHP.
As an interesting side-project, we performed analysis on the PHP malware sample and the IP addresses that the US government has provided as “…technical details regarding the tools and infrastructure used by Russian civilian and military intelligence services (RIS)”. [
Source]
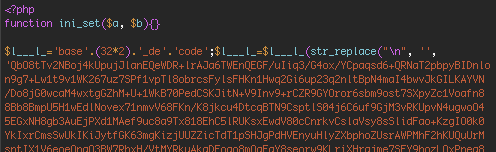
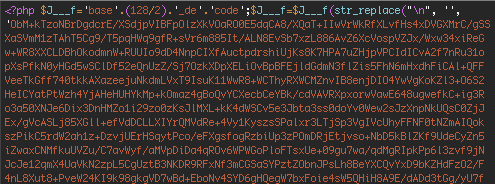
We used the PHP malware indicator of compromise (IOC) that DHS provided to analyze the attack data that we aggregate to try to find the full malware sample. We discovered that attackers use it to try to infect WordPress websites. We found it in the attacks that we block. Here it is.
The above is the header and here is the footer. The middle contains an encrypted block of text.
This is PHP malware that is uploaded to a server. An attacker then accesses the file in a browser and enters a password. The password also acts as a decryption key and decrypts the encrypted block of text which then executes. Once an attacker enters their password, it is stored in a cookie and they don’t need to enter the password again to access the malicious application.
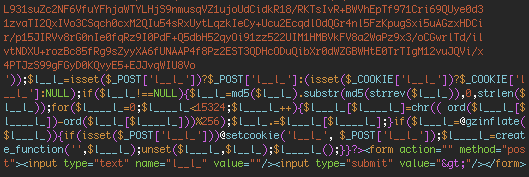
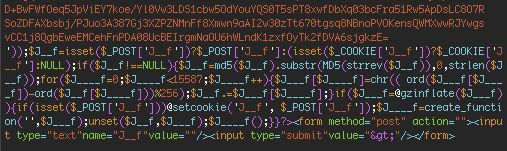
We managed to capture a request from an attacker that contained their password. It was ‘avto’ without quotes. We used the password to decrypt the block of encrypted text.
This is what the decrypted PHP looks like. It is a big chunk of PHP code that is a web shell.

We installed the web shell on a sandboxed environment. This is what it looks like:
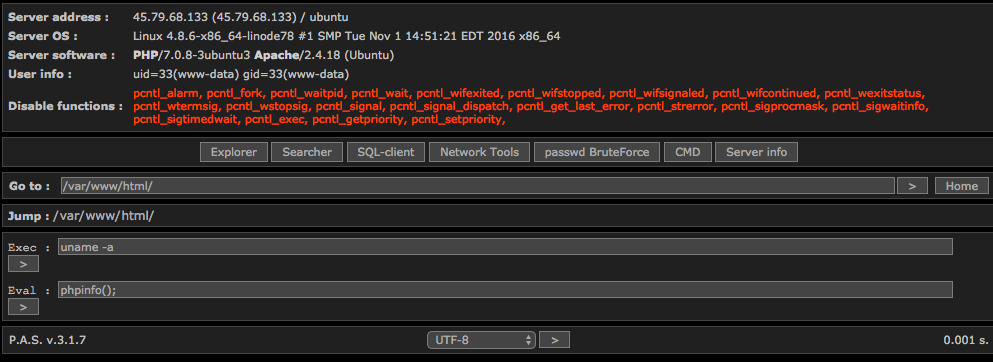
This is the kind of web shell that we see all the time in our day-to-day forensic operations. It includes the following basic features:
- File browser/explorer
- File search function
- A database client to download the contents of a hacked site database
- Network tools including a port scanner and the ability to bind a service to a port
- A tool to brute force attack passwords on FTP and POP3 services.
- A command line client to run arbitrary operating system commands
- A utility to view server configuration info
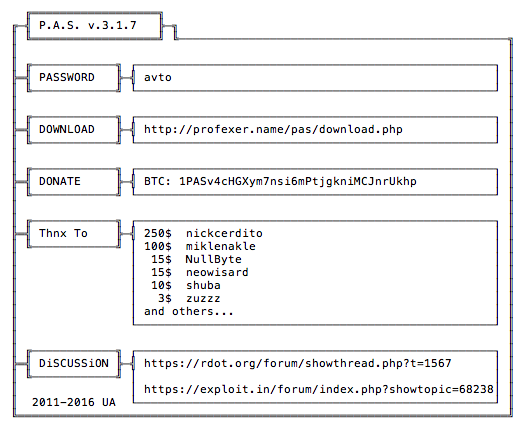
By viewing the source code, we could find the name of the malware and the version. It is P.A.S. 3.1.0.
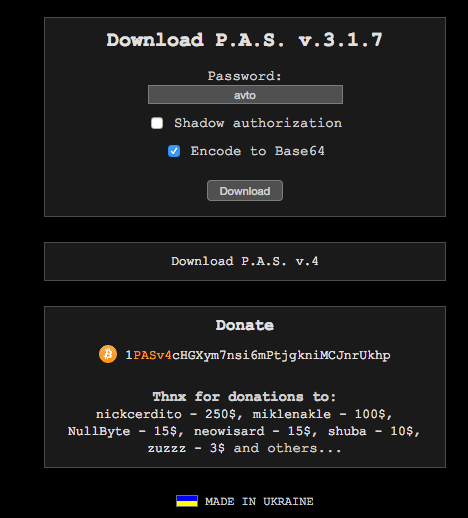
We googled it and found a website that makes this malware. You can find the site at this address:
http://profexer.name/pas/download.php
You can enter a password that you will use to access your malware once it’s installed and then hit ‘download’ and a ZIP file downloads.
The ZIP contains a text file and the malware. The text file looks like this:
The website claims the malware is made in Ukraine and the date at the bottom has the Ukraine country code UA.
This malware is
version 3.1.7 which is newer than the malware that the DHS indicator of compromise identifies. It is almost identical including it’s indentation:
And the footer:
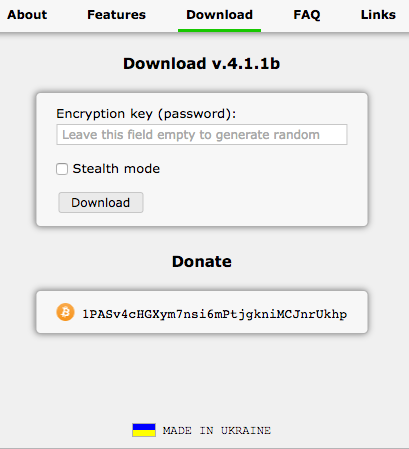
But PAS has evolved even further since 3.1.7. It is now version 4.1.1 which you can get from the same website:
The 4.1.1b info.txt file:
And the code has changed in 4.1.1 quite substantially. This is the header:
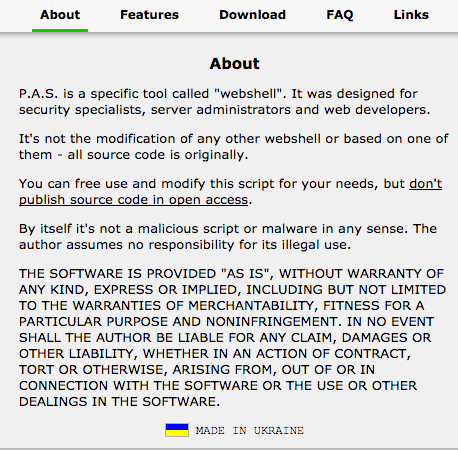
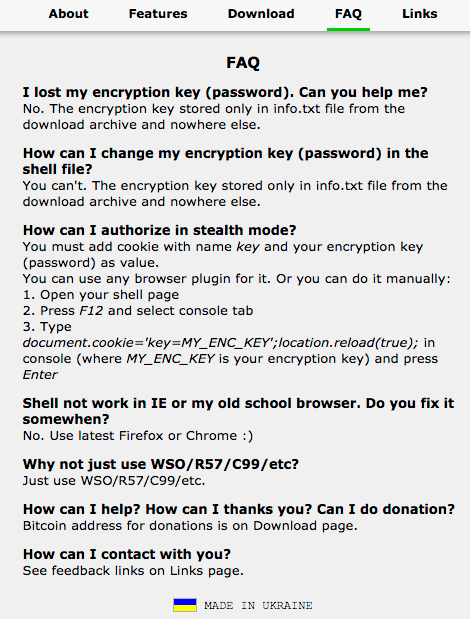
The PAS malware is user friendly. It has an About page:
They also have a helpful FAQ:
How does PAS infect WordPress websites?
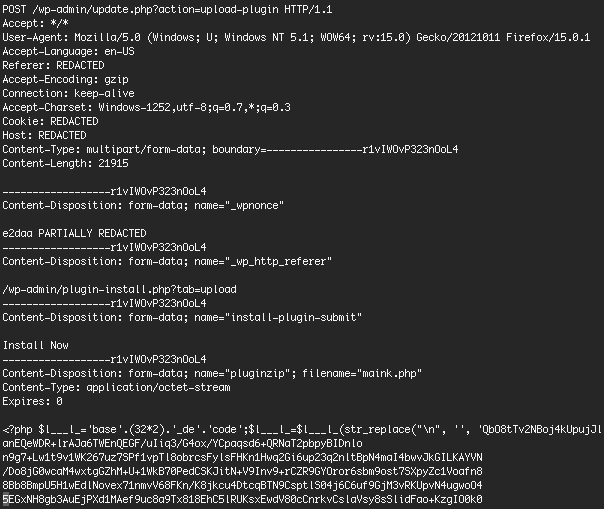
This is a typical infection attempt for PAS 3.1.0 which is the DHS sample:
The above request is an attempt to install a plugin in the WordPress CMS through the normal file upload method. What surprised us is that this request had a full set of cookies that indicates that the user or bot doing this was signed in and this probably was an actual web browser.
It also includes the WordPress nonce which is a security feature, also indicating this is a user. Only about 25% of the attacks that we see include the WordPress nonce, which suggests that many of these attempts fail.
The vast majority of attacks we see that try to infect with PAS 3.1.0 use this kind of request. Here are a few theories:
- WordPress website owners have malware installed on their workstations and that malware attempts to install PAS 3.1.0 on their WordPress websites.
- This is CSRF, or cross site request forgery attack, that installs the malware. This is unlikely because the nonce is present in many requests. A nonce is a security feature that prevents CSRF attacks.
- Users are voluntarily installing this on their own websites after downloading it from a malicious website thinking it is safe. Unlikely because the file that is uploaded is plain text PHP and it is clearly suspicious if you examine the file contents.
- Attackers are compromising websites through some other means and then using the compromised credentials to manually sign in and install PAS 3.1.0 with a standard browser. These sign-ins could be partially or fully automated.
Malware Conclusions
DHS and DNI have released a joint statement that says:
“
This document provides technical details regarding the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints associated with the U.S. election, as well as a range of U.S. Government, political, and private sector entities. The report contains specific indicators of compromise, including IP addresses and a PHP malware sample.”
The PHP malware sample they have provided appears to be P.A.S. version 3.1.0 which is commonly available and the website that claims to have authored it says they are Ukrainian. It is also several versions behind the most current version of P.A.S which is 4.1.1b. One might reasonably expect Russian intelligence operatives to develop their own tools or at least use current malicious tools from outside sources.
As you can see they are globally distributed with most of them in the USA.
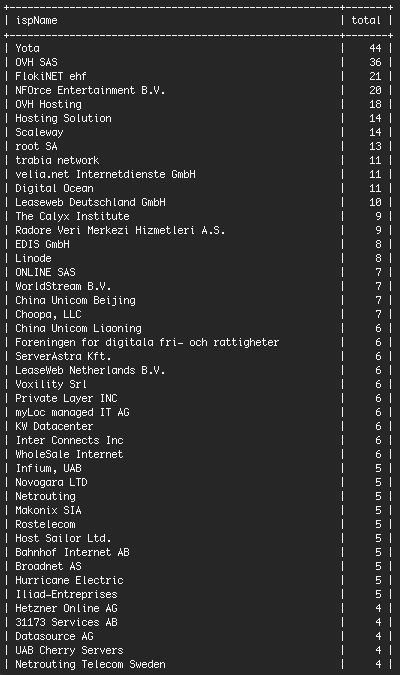
Lets look at who the top ISP’s are who own the IP addresses:
There are several hosting companies in the mix including
OVH SAS,
Digital Ocean,
Linode and
Hetzner. These are hosting companies that provide low cost hosting to WordPress customers and customers who use other PHP applications. A common pattern that we see in the industry is that accounts at these hosts are compromised and those hacked sites are used to launch attacks around the web.
Out of the 876 IP addresses that DHS provided, 134 or about
15% are Tor exit nodes, based on a reverse DNS lookup that we did on each IP address. These are anonymous gateways that are used by anyone using the Tor anonymous browsing service.
We examined our attack data to see which IP addresses in the DHS data are attacking our customer websites. We found a total of 385 active IP addresses during the last 60 days. These IP addresses have launched a total of
21,095,492 complex attacks during that 60 day period that were blocked by the
Wordfence firewall. We consider a complex attack to be an attack that tries to exploit a vulnerability to gain access to a target.
We also logged a total of
14,463,133 brute force attacks from these IP addresses during the same period. A brute force attack is a login guessing attack.
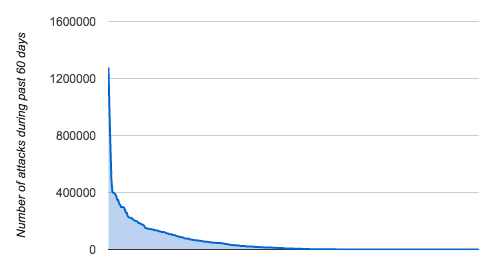
The chart below shows the distribution of the number of attacks per IP address. It only takes into account complex attacks. As you can see, a small number of the IP addresses that DHS provided as IOC’s are responsible for most of the attacks on WordPress websites that we monitor.
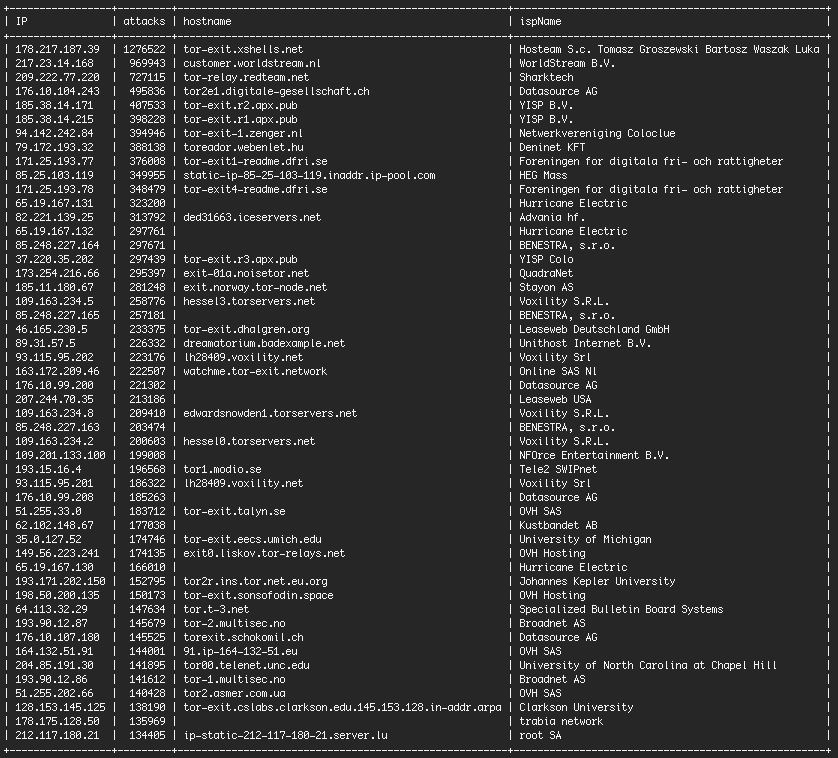
The following shows the list of the top 50 IP addresses in the DHS report sorted by the number of complex attacks we saw from each IP during the past 60 days.
As you can see, many of the top attacking IP addresses are Tor exit nodes. There is also a relatively small number of IP addresses launching most of the attacks on websites we monitor.
Conclusion regarding IP address data
What we’re seeing in this IP data is a wide range of countries and hosting providers. 15% of the IP addresses are Tor exit nodes. These exit nodes are used by anyone who wants to be anonymous online, including malicious actors.
Overall Conclusion
The IP addresses that DHS provided may have been used for an attack by a state actor like Russia. But they don’t appear to provide any association with Russia. They are probably used by a wide range of other malicious actors, especially the 15% of IP addresses that are Tor exit nodes.